Cyber-security is consistently one of the top concerns for business leaders across every industry and when you consider that the average cost of a breach is upwards of USD4.35 million[1], its no surprise why. While this focus has often led to investment and the implementation of robust security practices, it’s also forced cyber-criminals to rethink their attack strategies. Some of the most rapidly growing threat areas are identity-based attacks where malicious actors look to exploit identities, or the underlying infrastructure and policies that govern them. Identity Threat Detection and Response (ITDR) is an emerging security category designed to counter these types of attacks and help businesses streamline their identity protection.
At Microsoft, we see ITDR as the point where Identity and Access Management (IAM) meets Extended Detection and Response (XDR). The critical challenge organizations are faced with however, is in extending the necessary posture and protections across the entirety of their identity landscape. Modern Identity environments consist of multiple, often fragmented, components spanning on-premises infrastructure and the cloud. Leveraging our leadership and expertise in both Identity and Security, our goal has been to help our customers prevent, detect, and remediate identity-based attacks across their entire identity environment.
Detecting advanced attacks with threat level intelligence.
Through the years, we have seen identity attacks become more and more advanced with multifaceted strategies designed to exploit increasingly tiny gaps and establish a foothold from where attackers can move laterally. For instance, an initial compromise may begin with spear-phishing emails aimed at employees, tricking a few into unwittingly divulging their credentials. Armed with these stolen identities, they can exploit misconfigurations in the connections between on-premises and cloud identities to stealthily expand their reach into the connected cloud environments and applications. Other more sophisticated attacks focus on compromising identity infrastructure to mint their own certificates and navigate through the network, escalating their privileges and gaining deeper access as they go.
Analyzing 65 trillion signals daily from across Microsoft’s ecosystem of B2B and consumer offerings including Microsoft Azure, LinkedIn, Microsoft 365, and XBOX we are uniquely positioned to quickly spot emerging attack strategies and build detections for our customers. Some more recent examples you have may have heard of include: DnsHostName Spoofing, DFSCoerce, and KrbRelayUp tactics to name a few. Our ITDR strategy doesn’t stop there though, we further augment these powerful identity detections with correlated data from across security domains to deliver XDR-level insights and enhanced visibility across the kill-chain.
Powerful identity detections:
Let’s take a common tactic in identity attacks, lateral movement. While this may sound like a relatively simple use case, it requires robust monitoring and analysis of user activities across on-premises and cloud environments. Domain Controllers (DC) serve as the central authentication and authorization hub for on-premises networks and play a crucial role in managing who is given access to those resources. With the Microsoft Defender for Identity sensor installed on a Domain Controller, security leaders can see valuable information into user authentication events, account activities, and access permissions. Monitoring these logs can help identify suspicious activities like unauthorized account logins, privilege escalation attempts, or abnormal resource access.
Similarly, in cloud environments, Azure Active Directory (Azure AD) serves as a central identity and access management platform, sending valuable data to Microsoft Defender for Identity and the Security Operations Center teams. Leveraging Azure AD’s comprehensive auditing and monitoring capabilities as well as Azure Active Directory Identity Protection, organizations can track user sign-ins, access attempts, and other security-related events. By enabling Azure Active Directory Conditional Access policies, organizations can proactively detect and respond to anomalous activities or attack attempts, whether done in the cloud or on-premises. Some examples include simultaneous sign-ins from different locations, unusual access patterns, token replay attacks, or attacks aiming to take control of the identity infrastructure which may indicate unauthorized lateral movement between cloud and on-premises resources. See our documentation for more details on our identity detections.
Threat level intelligence:
To detect the sophisticated attack strategies we discussed earlier, identity detections alone are not enough. Microsoft Defender for Identity, the cornerstone of our identity security capabilities, is natively integrated within our XDR platform, Microsoft 365 Defender.
Microsoft 365 Defender offers unified visibility, investigation, and response across the cyber-attack kill chain. Leveraging AI and automation, it correlates alerts from different sources to provide a single incident view with rich contextual information. It also enables teams to quickly and efficiently investigate emerging threats. By corelating all the available information, including signals from endpoints, identity providers, identity infrastructure, collaboration tools and cloud applications, we can give a greater view into the entire end to end life cycle of the identity.
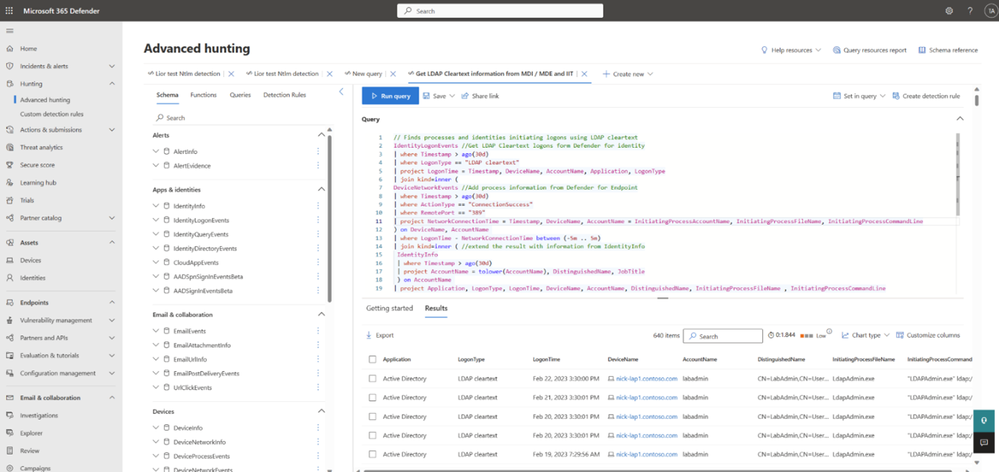
Figure 1: Advanced hunting tables[3] allow users to hunt for emerging threats across your identity data and activities within a single view, regardless of environment or provider. Create custom detections and enhance existing investigations with identity signals.
Respond and remediate attacks at machine speed.
When it comes to identity-based attacks, the ability to swiftly and effectively remediate the compromised systems and disrupt the attacker’s operations becomes crucial. For example, the median time for an attacker to access your private data after you fall victim to a phishing email is 1 hour, 12 minutes[4]. In a situation like this you need to be able to detect, investigate, and respond to the breach in under 72 minutes. Working across teams and tools this can be especially challenging, so we have focused on two critical areas to help our customers respond and remediate attacks at machine speed:
Enabling intelligent automation:
AI and automation are reshaping almost every facet of business today and security is no exception. A recent study in fact found organizations incurred 80% higher costs where security AI and automation weren’t fully deployed[1]. Capitalizing again on the native integration between our Identity protection capabilities and XDR platform, we leverage XDR-level intelligence and AI to automatically disrupt even the most advanced attacks.
Automatic attack disruption is designed to contain attacks in progress by automatically disabling or restricting compromised devices and user accounts—stopping progression and limiting the impact to organizations. This is a big innovation; today most security teams can’t respond fast enough to sophisticated attacks and are forced to reactively handle the fallout from a breach. With attack disruption, attacks are contained to a small number of assets, dramatically minimizing the impact and improving business continuity.
In an Identity attack, Microsoft Defender for Identity can take immediate action to disable the user, trigger multi-factor authentication, disable unauthorized accounts authentication using or even isolate affected systems using Microsoft Defender for Endpoint. These automated tactics not only limit the attacker’s ability to move laterally and access critical resources but also prevent further damage and data exfiltration.
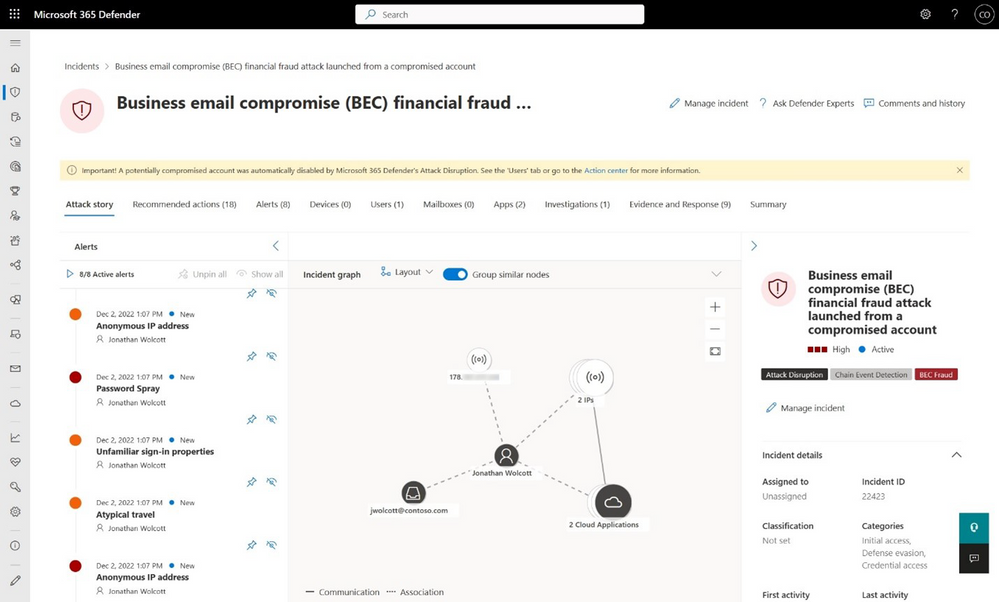
Figure 2: Incident view showing the yellow bar where automatic attack disruption took action
Maximizing user experience and efficiency.
ITDR is a team sport and while collaboration between SOC and Identity teams is crucial, each personas unique needs require distinctly different information and capabilities to do their job. At Microsoft we can help maximize your team’s effectiveness with integrated, persona-based experiences designed to surface and prioritize information and alerts.
SOC analysts gain greater visibility across their identity landscape with a unified Identity Inventory, showing all corporate identities in one, easy to search view. Going a layer deeper, Identity Pages offer more detailed information on each unique identity including recent behavior via the Identity Timeline. On top of all the Identity specific views and benefits, SOC teams can also capitalize on Microsoft’s Secure Score which correlates signals from across workloads to curate identity related recommendations and reduce your security posture risk.
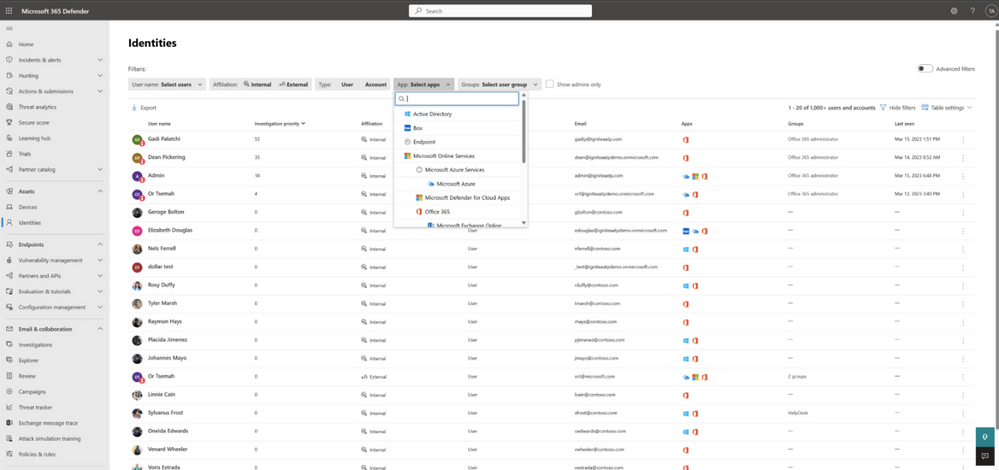
Figure 3: Identity Inventory delivers a comprehensive inventory of all your identities regardless of type, environment or vendor.

Figure 4: Identity page and Identity Activity Timeline view aggregate relevant data from multiple workloads to provides security teams will additional insight and detail into individual identities and recent behavior.
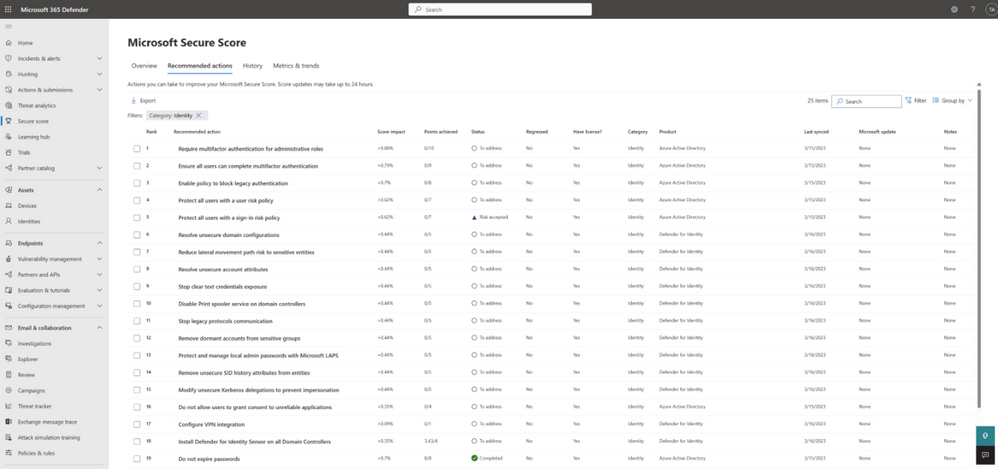
Figure 5: Microsoft Secure Score correlate signals from across workloads to curate and prioritize identity related recommendations and reduce your security posture risk.
Identity Admins and IT practitioners also benefit from their own unique portal and prioritized view where they can quickly sory by risk level and prevent potential account compromise.
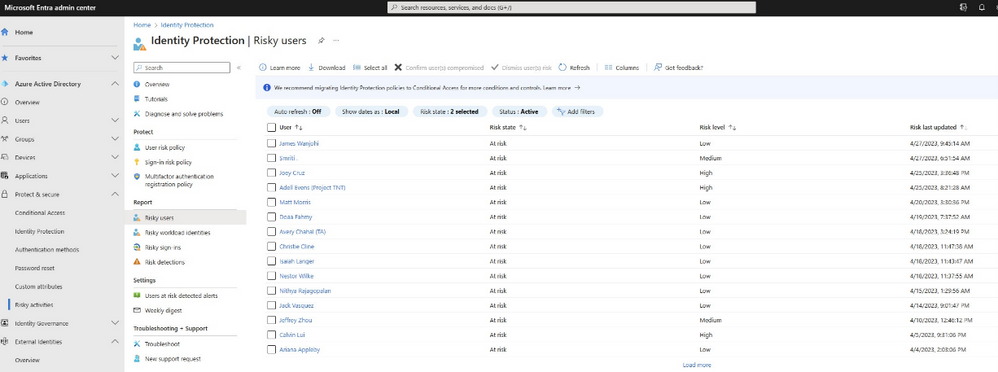
Figure 6: Azure Active Directory Identity Protection
Learn more about Microsoft’s ITDR strategy and find out how you can maximize your investments to save up to 60% with Microsoft 365 E5 Security and Microsoft 365 E5 Compliance[5].
———
[1] Ponemon Institute Cost of Breach Data 2021
[2] 17 Essential multi-factor authentication (mfa) statistics [2023], Jack Flynn. February 6, 2023.
[3] This feature is currently rolling out to public preview customers over the next couple of months, starting with defender for identity customers.
[4] Cyber Signals: 3 strategies for protection against ransomware, Vasu Jakkal. August 30, 2022.
[5] Savings based on publicly available estimated pricing for other vendor solutions and Web Direct/Base Price shown for Microsoft offerings .
