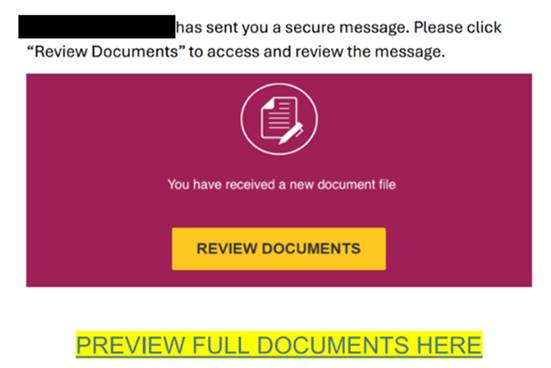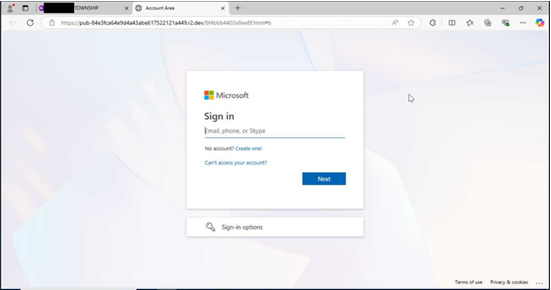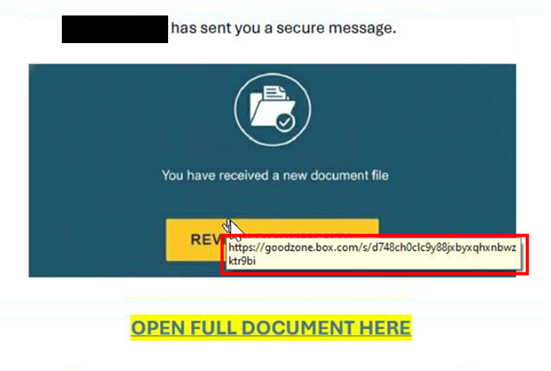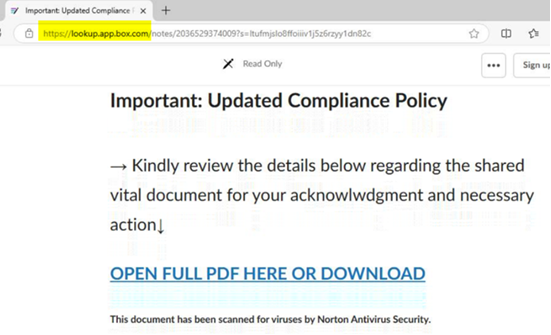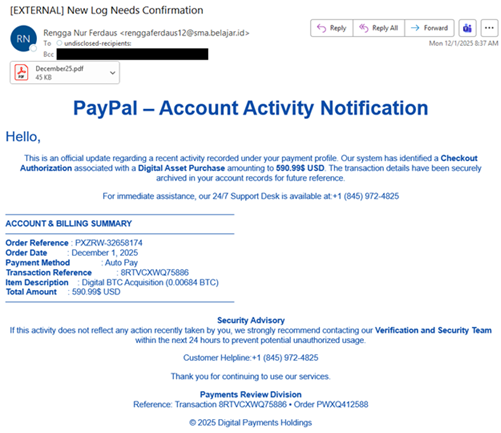
| The NJCCIC observed multiple Telephone-Oriented Attack Delivery (TOAD) campaigns targeting New Jersey State employees that purported to be legitimate notifications for purchases of digital assets or currencies. In one campaign, the email content lacks relevant context to the subject line phrases, such as “new log needs confirmation” or “update waiting for review.” The emails come from suspicious domains or out-of-country top-level domains (TLDs) and may contain an Adobe PDF attachment detailing the PayPal purchase. Another red flag is a purchase notification that is not personalized but sent to multiple recipients. Threat actors may add recipients in the “Bcc” field to appear more legitimate or circumvent some security filters that might identify emails sent to an extensive list in the “To” or “Cc” fields. In this campaign, threat actors create urgency by including a phone number if the target requires immediate assistance within the next 24 hours to dispute the “590.99$ USD” PayPal transaction. If the target calls the phone number, the threat actors impersonating a security team representative convince them to divulge sensitive information, such as account credentials or financial details, or download malicious software or a supposed remote support tool, which enables the threat actors to gain access to the device. |
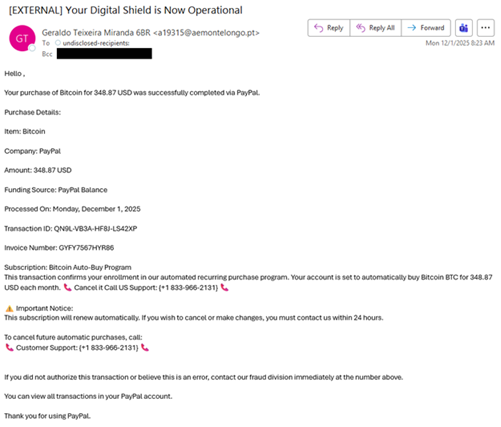
In a similar TOAD campaign, the subject line displays “your digital shield is now operational” and lacks relevant context to the email, which claims to be a Bitcoin purchase of “348.87 USD” via PayPal. The fraudulent transaction is part of an automated recurring purchase program or a monthly subscription. Threat actors provide a phone number for the target to cancel future automatic purchases or make changes within 24 hours.
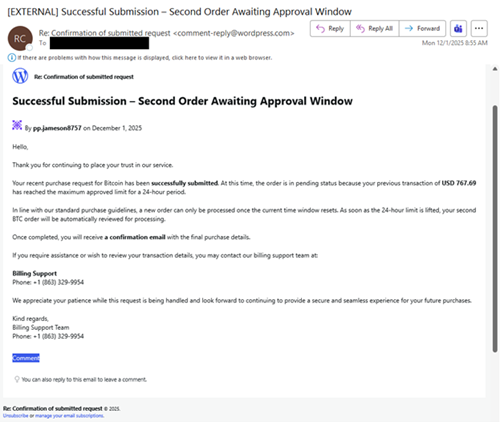
| In a separate campaign, the emails claim to be a Bitcoin purchase awaiting approval due to a previous transaction of “USD 767.69” reaching the maximum approved limit for a 24-hour period. They also include a billing support phone number for the target to call if they require assistance or wish to review the transaction details. Additionally, the fraudulent emails are disguised as WordPress notifications from the legitimate “comment-reply[@]wordpress[.]com” email address that facilitates blog comment notification and reply features. The threat actors abuse this service, hoping that their target will respond to the “posted” fraudulent purchase, either by calling the phone number or replying as a comment. |
| Recommendations |
| Refrain from clicking links, opening attachments, responding to, or acting on communications from unknown senders. Exercise caution with unsolicited communications from known senders or legitimate platforms. Scrutinize messages, especially those with urgent language or confirmation of updates, changes, or requests. Confirm messages from senders by verifying their contact information obtained from trusted and official sources before taking action, such as clicking on links or opening attachments. Type official website URLs into browsers manually and only submit account credentials, personal information, or financial details on official websites. Refrain from downloading or installing software from unknown sources. Keep systems and browsers up to date. Monitor accounts and statements for any unauthorized activity. Report malicious cyber activity to the NJCCIC and the FBI’s IC3. |