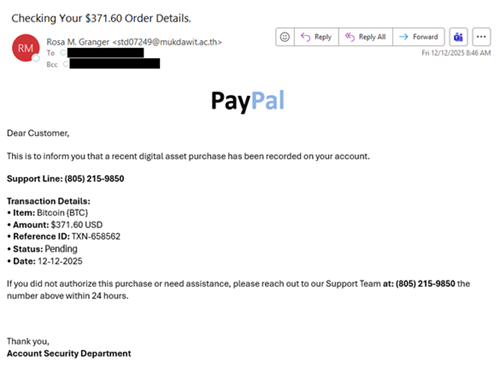
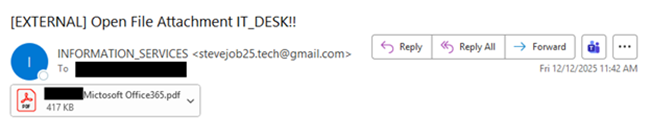
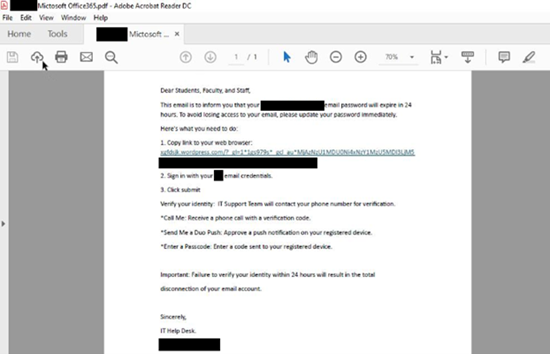
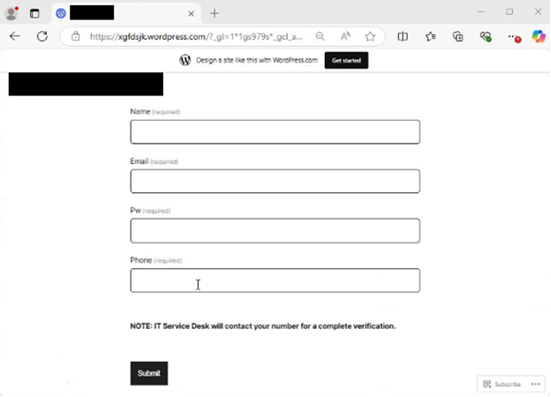
Hands Off my Tokens! NIST Seeks Comments on the Initial Public Draft of NIST Interagency Report 8587, Protecting Tokens and Assertions from Forgery, Theft, and Misuse through January 30, 2026.
What is in the Report?
Developed in coordination with CISA’s Joint Cyber Defense Collaborative and in response to Executive Order 14144, Sustaining Select Efforts to Strengthen the Nation’s Cybersecurity and Amending Executive Order 13694, NIST Interagency Report (IR) 8587 provides implementation guidance to help federal agencies and cloud service providers (CSPs) protect identity tokens and assertions from forgery, theft, and misuse.
Building on updates to NIST SP 800-53, the report outlines principles for CSPs and consuming agencies, details architectural considerations for identity providers and authorization servers, and recommends enhancements to key management, token verification, and lifecycle controls. The report also addresses threats demonstrated in recent high-profile attacks, emphasizes the importance of secure and configurable cloud services, and provides technical recommendations to safeguard single sign-on, federation, and application programming interface (API) access scenarios.
What kind of input is NIST seeking?
As an initial public draft, NIST IR 8587 is intended to gain critical feedback from stakeholders across government and industry. While comments are welcome and encouraged on all aspects of this document, NIST is particularly interested in the following five feedback areas:
- Signing Key Validity Periods. Feedback on the length of validity, the structure of the scenarios, and any additional feedback reviewers may have.
- Token Validity Periods. Opinions on token validity lengths and compensating controls that may impact commenters, particularly their availability, adoption, and use in government systems.
- Key Protection and Isolation. Feedback on the clarity and suitability of key management definitions and whether they are appropriately mapped to FISMA system classification levels.
- Key Scoping. Sharing of operational considerations, implementation challenges, and best practices that could strengthen these recommendations.
- Emerging Standards. Comments about emerging standards and protocols that might support the technical achievement of token and assertion protection outcomes (e.g., Demonstrated Proof-of-Possession, Global Revocation).
The public comment period is open through January 30, 2026.
Please submit your comments and share your feedback with us via email at iam@list.nist.gov.Read More