I get ask all the time for tools or tricks that a administrator can use here a great one. AD Unlocker Pro.
You and administrator of a Active Directory Domain you don your due diligence and set a group policy that say after x tries lock user account , Now how do you audit and see what accounts are locked?
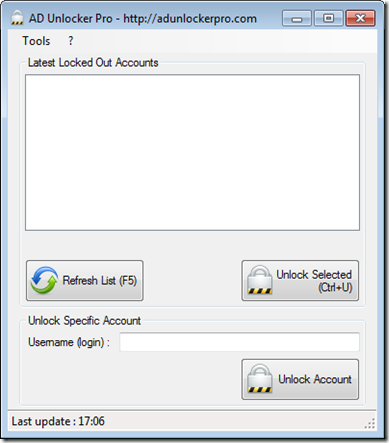
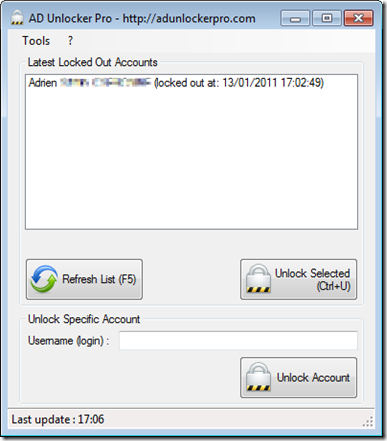
Here a very small utility that you can run that will show you what accounts are locked and Unlocking them with only one click.
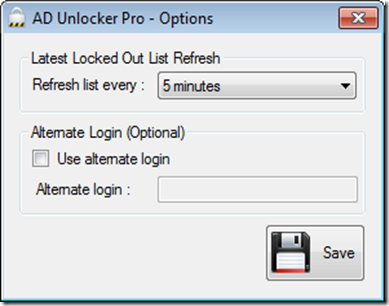
This application also can use alternate login (useful if your Active Directory Administrator account is not your default user account).
See the accounts
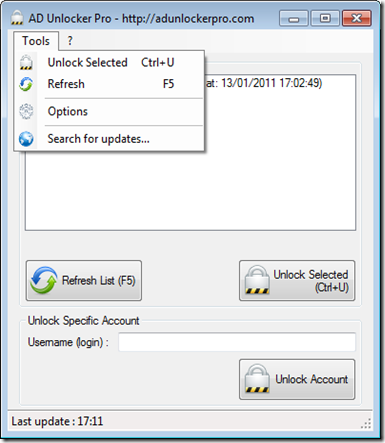
Choose what account to unlock
and you can ever have application running to show when account is locked
For those of you who read my blog daily here a great deal
TODAY 2/24/2011 you can download and get a free copy
by clicking Here (follow the directions)