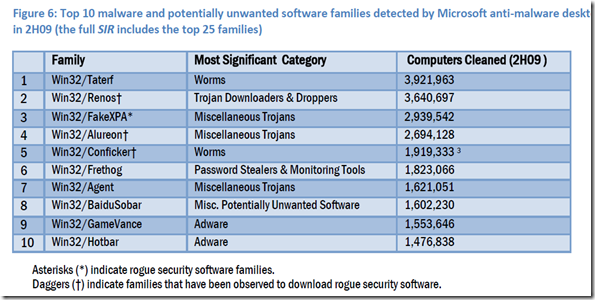
AS a security profession i am always on the look for tools that we help me do easer. Ipswich has just offered a free tool that should be in any Windows administrator took kit.
The Engineer’s Toolkit has a single login and credentials library, features robust functionality, and is designed to simplify common network engineering tasks. The Engineer’s Toolkit can help you with:
* Network design and planning
* DNS verification
* Network diagnostics
* Remote access to devices and servers
* Network discovery
* Configuration and credential management
Your role as a network engineer is not an easy one. Routine tasks often take more time than planned and troubleshooting issues can lead to long days, not to mention a few headaches.
Take advantage of our limited time offer -Get the WhatsUp Gold Engineer’s Toolkit today for free! Get ready to simplify network engineering.
Download your WhatsUp Gold Engineer’s Toolkit(http://www.whatsupgold.com/2/engineerstoolkit) today and gain access to the most robust and usable toolkit available featuring one application, one interface, and one easy way to monitor, diagnose and troubleshoot network issues!