Threat actors continue to impersonate recruiters and employers to target potential job seekers with fake or unrealistic remote job offers. They often send unsolicited emails or text messages that promise high pay for little work, require payment to get a job or training, lure targets with bad checks to buy fake work equipment or supplies, involve repackaging or shipping items often purchased with stolen credit cards, or request personal data, leading to financial loss and identity theft. Over the past month, the NJCCIC has observed an increase in remote job scams targeting New Jersey State employees and residents
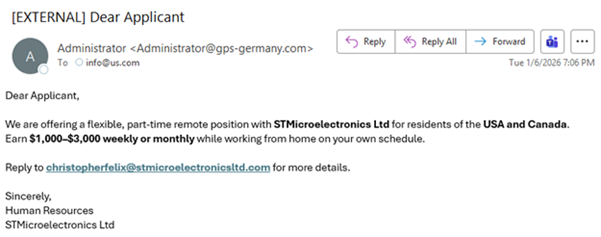
Threat actors are targeting New Jersey State employees in this latest job scam. They claim to represent Human Resources for an organization that is not the same as the sender’s domain. Another red flag is that the reply-to email address is in the body of the email and does not match the sender’s email address. They offer an unrealistic part-time remote job opportunity targeting US and Canadian residents and use a generic “Dear Applicant” greeting
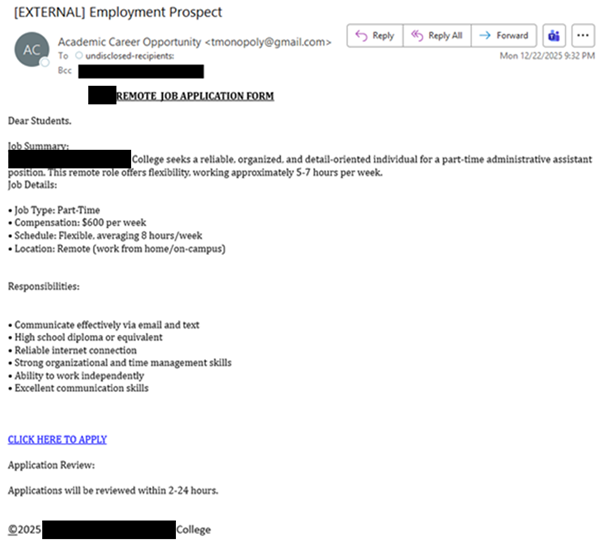
| In another campaign, threat actors impersonate an educational institution to encourage their targets to apply for a remote job. Instead of using the official educational institution’s domain, the emails are sent from a Gmail account to multiple New Jersey State employees in the BCC field and use a generic “Dear Students” greeting. Threat actors claim a quick turnaround to convince their targets to act quickly and apply by stating that applications will be reviewed within two to 24 hours. If the “CLICK HERE TO APPLY” link is clicked, targets are directed to a Microsoft Forms page to capture sensitive information. Additionally, the copyright symbol at the bottom of the email is hyperlinked to a Microsoft phishing page to steal account credentials. |
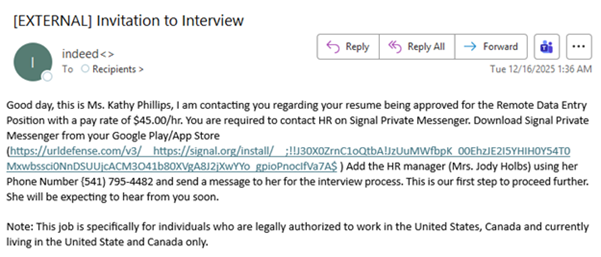
In the above campaign, threat actors claim to be recruiters expressing interest in the target’s resume for an interview for the purported remote position. The email is sent to multiple recipients and claims to be an Indeed interview invitation. Legitimate Indeed communications are more customized and formal and sent directly through the Indeed account. The threat actors request that the target contacts Human Resources for more information about the interview process via Signal by clicking on the link. Legitimate companies or recruiters typically do not conduct interviews through such instant messaging platforms.

| Threat actors continue to target unsuspecting job seekers via text messages, initiating unsolicited conversations about potential job opportunities. The message outlines the position’s benefits, including flexible hours, competitive earnings, remote work opportunities, training, and requirements. If the target responds with “Yes,” the threat actors send a phishing link or attempt to persuade them to continue the conversation on a different platform to disclose their personal information, such as a Social Security number (SSN), a photo of their driver’s license, and banking information, supposedly to set up direct deposit. |
| The NJCCIC also received reports of threat actors impersonating a recruiter from hire-desk[.]com. The malicious email contains a Calendly scheduling link and a Google Meet invitation link. Calendly links are used in phishing campaigns to direct targets to malicious websites that request sensitive information or account credentials. Google Meet users can join meetings on mobile phones or tablets via the Google Meet app, or they can connect from their computer browser, as the software does not require installation. The red flag in this campaign is the Google Meet link that prompts the target to install a “GoogleMeetSetup[.]exe” file, disguised as a remote monitoring and management (RMM) tool. This trojanized installer is used for initial access and persistence to commit further malicious activity. |
| Recommendations |
| Exercise caution with unsolicited communications from unknown senders or legitimate organizations and platforms. Confirm requests from senders using contact information obtained from verified and official sources before taking action, such as clicking links or opening attachments or files. Consider contacting the company’s human resources department to verify if the job offer is legitimate and if the person is indeed employed there. Type official website URLs into browsers manually and only submit sensitive information on official websites. Be careful when posting your resume publicly, as this information can be misused to exploit you. Refrain from job offers that do not involve a phone or video interview, lack specific duties and company information, and create a sense of urgency and pressure to provide personal information quickly. Keep systems and browsers up to date. Ignore and block suspicious emails and phone numbers. Report malicious cyber activity to the NJCCIC, the FBI’s IC3, and the FTC. |