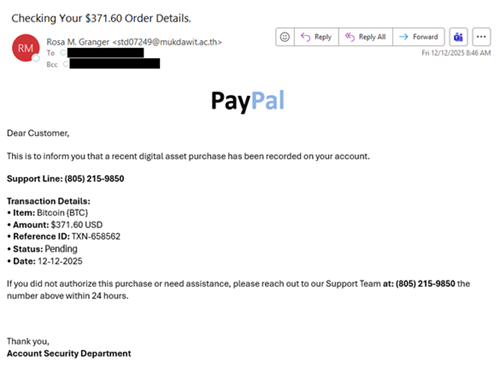
| The NJCCIC detected a new telephone-oriented attack delivery (TOAD) campaign. Unlike most phishing attempts, TOAD attacks do not include malicious attachments or URLs in their initial messages. The aim of the message is to trick an unwary user into calling the provided number. Upon receiving a call, threat actors employ further social engineering tactics to convince a target to install malware, grant full remote control, or enter credentials on a malicious webpage. |
| The threat actors behind this campaign impersonate PayPal order receipts for Bitcoin, using the PayPal logo and transaction details to make the email appear legitimate. Currently, they make no attempts to obfuscate the sender’s email address, which is a red flag for malicious emails. Finally, the email includes a contact phone number and a 24-hour deadline to dispute the transaction, creating a sense of urgency to prevent victims from realizing that something is amiss. |
| Recommendations |
| Facilitate user awareness training to include these types of phishing-based techniques. Confirm requests from senders via contact information obtained from verified and official sources. Review the Don’t Take the Bait! Phishing and Other Social Engineering Attacks NJCCIC product for more information on common phishing and social engineering attacks. Ensure multi-factor authentication (MFA) is enabled for all online accounts. If you suspect an account has been compromised, change the account’s password immediately and add a secondary authentication method. Report other malicious cyber activity to the NJCCIC and the FBI’s IC3. |