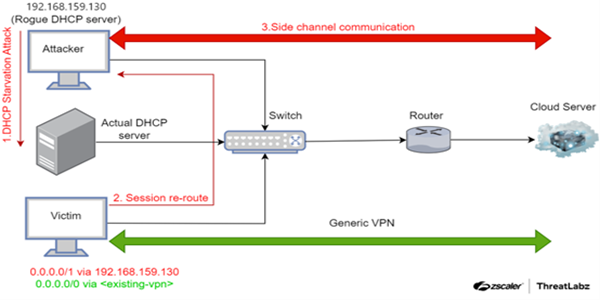
| A VPN bypass technique dubbed TunnelVision was discovered that allows an unauthenticated user to send DHCP messages to manipulate routes to redirect VPN traffic. This vulnerability may allow a threat actor to read, disrupt, or modify network traffic expected to be protected by the VPN. If successfully exploited, the existing VPN tunnel remains intact, and the side channel created by the threat actor is undetectable. This “decloaking” method is identified as CVE-2024-3661. Recommendations and technical details can be found in the Zscaler blog post and the Leviathan Security blog post. |