- Reporting a scam is your best line of defense against cyber incidents. Don’t hesitate to call out phishing attempts. Learn more: https://staysafeonline.org/theft-fraud-cybercrime/phishing/ #CybersecurityAwarenessMonth
- Most cyber incidents start with a phish. To stop it, report it. Learn more: https://staysafeonline.org/theft-fraud-cybercrime/phishing/ #CybersecurityAwarenessMonth
- Cybercriminals cast wide nets with #phishing tactics, hoping to drag in victims. They may offer a financial reward, threaten you if you don’t engage, or claim that someone is in need of help. Stop, take a moment, and think before you click. Learn more: https://staysafeonline.org/theft-fraud-cybercrime/phishing/ #CybersecurityAwarenessMonth
- Tips for Spotting a Phish: 1) They create a sense of urgency or claim to need help. 2) They ask for your personal info. 3) They want you to download a file or click on a link. Learn more: https://staysafeonline.org/theft-fraud-cybercrime/phishing/ #CybersecurityAwarenessMonth
- Think before you click! Phishing emails disguise themselves as harmless messages, but they’re actually dangerous digital piranhas swimming in your inbox. Stay vigilant, spot the signs, and report those fraudulent emails. Together, we can #StaySafeOnline! Learn more: https://staysafeonline.org/theft-fraud-cybercrime/phishing/ #CybersecurityAwarenessMonth
- Don’t get hooked! Phishing emails are like sneaky bait trying to reel you in. Learn how to spot them and report those fishy attempts to keep your inbox clean and your personal information safe. Learn more: https://staysafeonline.org/theft-fraud-cybercrime/phishing/ #CybersecurityAwarenessMonth
- Phishing: The art of deception. Cybercriminals are getting crafty, sending emails that look legit but aim to steal your information. Trust your gut, stay cautious, and report those phishing emails. Learn more: https://staysafeonline.org/theft-fraud-cybercrime/phishing/ #CybersecurityAwarenessMonth
- Your inbox is your fortress! Phishing emails try to breach your defenses, but you can outsmart them. Learn the telltale signs of phishing, such as misspellings, suspicious attachments, or urgent requests, and report those fraudulent messages. Learn more: https://staysafeonline.org/theft-fraud-cybercrime/phishing/ #CybersecurityAwarenessMonth
Year: 2023
Multi-factor authentication
- Make it harder for cybercriminals to access your account by enabling multi-factor authentication. Learn more: https://staysafeonline.org/online-safety-privacy-basics/multi-factor-authentication/ #CybersecurityAwarenessMonth
- Multi-factor authentication adds an extra layer of protection to your accounts, making it harder for hackers to get in. Stay one step ahead and lock them out! Learn more: https://staysafeonline.org/online-safety-privacy-basics/multi-factor-authentication/
- Where should you use MFA?
1. On accounts with your financial info like banks, or online stores
2. On accounts with personal info, like social media
3. On accounts with info you use for work
TLDR: Use MFA everywhere!
Learn more: https://staysafeonline.org/online-safety-privacy-basics/multi-factor-authentication/ #CybersecurityAwarenessMonth
Adding MFA to an account greatly increases your security. It may include:
- A biometric identifier like a fingerprint
- A unique number yes or no prompt generated by an authenticator app
Learn more: https://staysafeonline.org/online-safety-privacy-basics/multi-factor- authentication/ #CybersecurityAwarenessMonth
Learn more: https://staysafeonline.org/online-safety-privacy-basics/multi-factor-authentication/ #CybersecurityAwarenessMonth
- Adding MFA to an account greatly increases your security. It may include:
- A code emailed to an account or texted
- A biometric identifier like a fingerprint
- A unique number yes or no prompt generated by an authenticator app
Learn more: https://staysafeonline.org/online-safety-privacy-basics/multi-factor- authentication/ #CybersecurityAwarenessMonth
- Passwords are like the gatekeepers of your online kingdom! But why settle for one guard when you can have two? Multi-factor authentication doubles the security, making your accounts nearly impenetrable. Keep the baddies at bay! Learn more: https://staysafeonline.org/online-safety-privacy-basics/multi-factor-authentication/ #CybersecurityAwarenessMonth
- There’s no one like you in the whole world… except the cybercriminal with your password. Don’t get hacked. Use multi-factor authentication. Learn more: https://staysafeonline.org/online-safety-privacy-basics/multi-factor-authentication/ #CybersecurityAwarenessMonth
- One lock, two locks, three locks…who needs a keychain? With multi-factor authentication, you’re like an expert online locksmith! Don’t give hackers an easy way in. Protect your accounts and sleep like a baby! Learn more: https://staysafeonline.org/online-safety-privacy-basics/multi-factor-authentication/ #CybersecurityAwarenessMonth
CISA Community Bulletin Special Edition: Cybersecurity Awareness Month 2023
The Final Countdown to Cybersecurity Awareness Month 2023
Since 2004, the President of the United States and Congress have declared the month of October to be Cybersecurity Awareness Month, helping individuals protect themselves online as threats to technology and confidential data become more commonplace. The Cybersecurity and Infrastructure Security Agency (CISA) and the National Cybersecurity Alliance (NCA) are working together to create resources and messaging for organizations to use when they talk with their employees and customers, and information for the public, about staying safe online.
2023 marks the 20th Cybersecurity Awareness Month, and this year CISA is launching a new theme that will encourage actions we can take, and online behaviors we can change, to reduce cyber risk not only during Cybersecurity Awareness Month, but every day throughout the year.
The new theme will be announced in time for Cybersecurity Awareness Month. In the meantime, we encourage you to share the important actions and key messages below:
- Turn on multifactor authentication (MFA): You need more than a password to protect your online accounts, and enabling MFA makes you significantly less likely to get hacked.
- Use strong passwords: Use passwords that are long, unique, and randomly generated. Use password managers to generate and remember these unique passwords for each of your accounts. A password manager will encrypt passwords and secure them for you!
- Recognize & report phishing: If a link looks a little off, think before you click. It could be an attempt to get sensitive information or install malware.
- Update your software: Don’t delay – If you see a software update notification, act promptly. Better yet, turn on automatic updates.
The following materials will also be made available later this summer to help you promote your organization’s participation in Cybersecurity Awareness Month and create your own campaign:
· Partner Toolkit
· Tipsheets on the Four Key Behaviors
· Cybersecurity Awareness Month 101 Presentation
· Sample Social Media Posts & Graphics
· And More!
For more information, and to become a CISA Cybersecurity Awareness Month partner, contact us at AwarenessCampaigns@cisa.dhs.gov.
Microsoft Blog: Midnight Blizzard conducts targeted social engineering over Microsoft Teams
Microsoft Threat Intelligence has identified highly targeted social engineering attacks using credential theft phishing lures sent as Microsoft Teams chats by the threat actor that Microsoft tracks as Midnight Blizzard (previously tracked as NOBELIUM). This latest attack, combined with past activity, further demonstrates Midnight Blizzard’s ongoing execution of their objectives using both new and common techniques. In this latest activity, the threat actor uses previously compromised Microsoft 365 tenants owned by small businesses to create new domains that appear as technical support entities. Using these domains from compromised tenants, Midnight Blizzard leverages Teams messages to send lures that attempt to steal credentials from a targeted organization by engaging a user and eliciting approval of multifactor authentication (MFA) prompts. As with any social engineering lures, we encourage organizations to reinforce security best practices to all users and reinforce that any authentication requests not initiated by the user should be treated as malicious.
Our current investigation indicates this campaign has affected fewer than 40 unique global organizations. The organizations targeted in this activity likely indicate specific espionage objectives by Midnight Blizzard directed at government, non-government organizations (NGOs), IT services, technology, discrete manufacturing, and media sectors. Microsoft has mitigated the actor from using the domains and continues to investigate this activity and work to remediate the impact of the attack. As with any observed nation-state actor activity, Microsoft has directly notified targeted or compromised customers, providing them with important information needed to secure their environments.
Midnight Blizzard (NOBELIUM) is a Russia-based threat actor attributed by the US and UK governments as the Foreign Intelligence Service of the Russian Federation, also known as the SVR. This threat actor is known to primarily target governments, diplomatic entities, non-government organizations (NGOs), and IT service providers primarily in the US and Europe. Their focus is to collect intelligence through longstanding and dedicated espionage of foreign interests that can be traced to early 2018. Their operations often involve compromise of valid accounts and, in some highly targeted cases, advanced techniques to compromise authentication mechanisms within an organization to expand access and evade detection.
Midnight Blizzard is consistent and persistent in their operational targeting, and their objectives rarely change. They utilize diverse initial access methods ranging from stolen credentials to supply chain attacks, exploitation of on-premises environments to laterally move to the cloud, exploitation of service providers’ trust chain to gain access to downstream customers, as well as the Active Directory Federation Service (AD FS) malware known as FOGGYWEB and MAGICWEB. Midnight Blizzard (NOBELIUM) is tracked by partner security vendors as APT29, UNC2452, and Cozy Bear.
Midnight Blizzard’s latest credential phishing attack
Midnight Blizzard regularly utilizes token theft techniques for initial access into targeted environments, in addition to authentication spear-phishing, password spray, brute force, and other credential attacks. The attack pattern observed in malicious activity since at least late May 2023 has been identified as a subset of broader credential attack campaigns that we attribute to Midnight Blizzard.
Use of security-themed domain names in lures
To facilitate their attack, the actor uses Microsoft 365 tenants owned by small businesses they have compromised in previous attacks to host and launch their social engineering attack. The actor renames the compromised tenant, adds a new onmicrosoft.com subdomain, then adds a new user associated with that domain from which to send the outbound message to the target tenant. The actor uses security-themed or product name-themed keywords to create a new subdomain and new tenant name to lend legitimacy to the messages. These precursory attacks to compromise legitimate Azure tenants and the use of homoglyph domain names in social engineering lures are part of our ongoing investigation. Microsoft has mitigated the actor from using the domains.
Social engineering attack chain
In this activity, Midnight Blizzard either has obtained valid account credentials for the users they are targeting, or they are targeting users with passwordless authentication configured on their account – both of which require the user to enter a code that is displayed during the authentication flow into the prompt on the Microsoft Authenticator app on their mobile device.
After attempting to authenticate to an account where this form of MFA is required, the actor is presented with a code that the user would need to enter in their authenticator app. The user receives the prompt for code entry on their device. The actor then sends a message to the targeted user over Microsoft Teams eliciting the user to enter the code into the prompt on their device.
Step 1: Teams request to chat
The target user may receive a Microsoft Teams message request from an external user masquerading as a technical support or security team.

Step 2: Request authentication app action
If the target user accepts the message request, the user then receives a Microsoft Teams message from the attacker attempting to convince them to enter a code into the Microsoft Authenticator app on their mobile device.

Step 3: Successful MFA authentication
If the targeted user accepts the message request and enters the code into the Microsoft Authenticator app, the threat actor is granted a token to authenticate as the targeted user. The actor gains access to the user’s Microsoft 365 account, having completed the authentication flow.
The actor then proceeds to conduct post-compromise activity, which typically involves information theft from the compromised Microsoft 365 tenant. In some cases, the actor attempts to add a device to the organization as a managed device via Microsoft Entra ID (formerly Azure Active Directory), likely an attempt to circumvent conditional access policies configured to restrict access to specific resources to managed devices only.
Recommendations
Microsoft recommends the following mitigations to reduce the risk of this threat.
- Pilot and start deploying phishing-resistant authentication methods for users.
- Implement Conditional Access authentication strength to require phishing-resistant authentication for employees and external users for critical apps.
- Specify trusted Microsoft 365 organizations to define which external domains are allowed or blocked to chat and meet.
- Keep Microsoft 365 auditing enabled so that audit records could be investigated if required.
- Understand and select the best access settings for external collaboration for your organization.
- Allow only known devices that adhere to Microsoft’s recommended security baselines.
- Educate users about social engineering and credential phishing attacks, including refraining from entering MFA codes sent via any form of unsolicited messages.
- Educate Microsoft Teams users to verify ‘External’ tagging on communication attempts from external entities, be cautious about what they share, and , and never share their account information or authorize sign-in requests over chat.
- Educate users to review sign-in activity and mark suspicious sign-in attempts as “This wasn’t me”.
- Implement Conditional Access App Control in Microsoft Defender for Cloud Apps for users connecting from unmanaged devices.
Indicators of compromise
| Indicator | Type | Description |
| msftprotection.onmicrosoft[.]com | Domain name | Malicious actor-controlled subdomain |
| identityVerification.onmicrosoft[.]com | Domain name | Malicious actor-controlled subdomain |
| accountsVerification.onmicrosoft[.]com | Domain name | Malicious actor-controlled subdomain |
| azuresecuritycenter.onmicrosoft[.]com | Domain name | Malicious actor-controlled subdomain |
| teamsprotection.onmicrosoft[.]com | Domain name | Malicious actor-controlled subdomain |
Hunting guidance
Microsoft Purview
Customers hunting for related activity in their environment can identify users that were targeted with the phishing lure using content search in Microsoft Purview. A content search can be created for selected Exchange mailboxes (which include Teams messages) using the following keywords (remove the [] around the “.” before use):
- msftprotection.onmicrosoft[.]com
- identityVerification.onmicrosoft[.]com
- accountsVerification.onmicrosoft[.]com
- azuresecuritycenter.onmicrosoft[.]com
- teamsprotection.onmicrosoft[.]com
- We detected a recent change to your preferred Multi-Factor Authentication (MFA)
The search results will include the messages that match the criteria. The first result will appear to be from <threadid>@unq.gbl.spaces addressed to the target user and the threat actor (i.e., the request to chat as described in Step 1), followed by the message sent by the threat actor, as shown in the Microsoft Purview image below:

Microsoft Sentinel
Microsoft Sentinel customers can use the TI Mapping analytics (a series of analytics all prefixed with “TI map”) to automatically match indicators associated with Midnight Blizzard in Microsoft Defender Threat Intelligence with data in their workspace. If the TI Map analytics are not currently deployed, customers can install the Threat Intelligence solution from the Microsoft Sentinel Content Hub to have the Defender Threat Intelligence connector and analytics rule deployed in their Sentinel workspace. Learn more about the Content Hub.
Microsoft Sentinel also has a range of detection and threat hunting content that customers can use to detect activity related to the activity described in this blog:
- Azure portal sign-in from another Azure tenant
- Successful sign-in from non-compliant device
- User accounts – Sign-in failure due to CA spikes
- New onmicrosoft domain added to tenant
Further reading
Read about the threat actor Midnight Blizzard (formerly tracked as NOBELIUM).
Mozilla Releases Security Updates for Firefox and Firefox ESR
Mozilla has released security updates to address vulnerabilities for Firefox 116, Firefox ESR 115.1, and Firefox ESR 102.14. An attacker could exploit some of these vulnerabilities to take control of an affected system.
CISA encourages users and administrators to review Mozilla’s security advisories for Firefox 116, Firefox ESR 115.1, and Firefox ESR 102.14 for more information and apply the necessary updates.
Free Microsoft e-books: Empower your workforce with a new partner in productivity.
| Get the e-book |
| For years now, AI has played a crucial role behind the scenes, powering everything from online searches to personalized streaming recommendations. Now, we are entering a transformative phase where AI is no longer just an unseen assistant but a powerful partner in enhancing productivity. Download the Working Smarter with AI e-book to: Discover the untapped potential of language models and generative AI and explore innovative ways to leverage their capabilities.Gain valuable insights on how to ensure the secure and responsible use of AI, including how to build an ethical and transparent AI ecosystem.Learn how to maximize the intelligent features of Copilot and enable your workforce to achieve its potential. |
Wi-Fi vulnerability in Canon inkjet printers may expose user information.
Description
Sensitive information on the Wi-Fi connection settings stored in the memories of inkjet printers (home and office/large format) may not be deleted by the usual initialization process.
Affected Products/Versions
Please check the affected inkjet printer models from here.
Mitigation/Remediation
When your printer may be in the hand of any third party, such as when repairing, lending or disposing the printer, take the following steps from the printer unit:
- Reset all settings (Reset settings ‐> Reset all)
- Enable the wireless LAN
- Reset all settings one more time
For models that do not have the Reset all settings function, take the following steps:
- Reset LAN settings
- Enable the wireless LAN
- Reset LAN settings one more time
Please refer to the operation manual of relevant model for specific Reset all or Reset LAN settings.
Go here for more details
New Microsoft Sentinel blog: Automate tasks management to protect your organization against threats
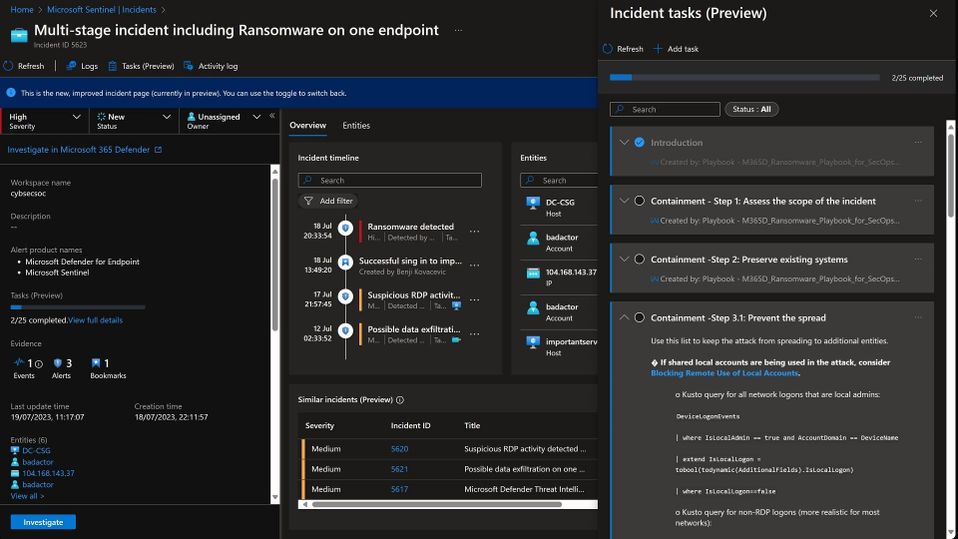
When investigating an incident, analysts follow certain steps – tasks – to ensure that the investigation is conducted effectively and efficiently. Standardizing the process is necessary for both generic steps and specific types of incidents, and their availability in the context of the incident allows for faster and more efficient management and remediation.
Tasks in Microsoft Sentinel can help security analysts streamline their workflow and improve their efficiency. Analysts can add tasks to specific incidents or alerts, enabling them to track the progress of investigations and remediation activities. While tasks can be added manually from within the Sentinel console, playbooks, and automation rules can be used to automatically create tasks based on certain conditions. Today we’re happy to announce the release of new playbooks, a workbook, and Log Analytics logs as well as an update to the SOC Process Framework. Along with a new integration with Microsoft 365 Defender SecOps playbooks, this will allow even more efficiency in managing incidents and the SOC’s tasks, with out-of-the-box content delivered by our security experts.
New playbooks with tasks for BEC, Ransomware, and Phishing investigation
Handling complex incidents can be a long, challenging task that requires lots of expertise in different fields. Microsoft 365 Defender SecOps workflows offer security analysts a detailed guided response playbook for investigating and responding to security incidents, including Phishing, Ransomware, and BEC. Developed by some of the world’s top security researchers and backed by Microsoft’s extensive experience in threat detection and response, these workflows provide unparalleled security value, significantly bolstering an organization’s defenses.. And now, with dedicated playbooks in Sentinel, these workflows can be easily transformed into tasks. Simply deploy the phishing, BEC, and ransomware playbooks in your workspace and apply them to the corresponding incidents. By integrating Defender workflows with Sentinel tasks, security teams can enjoy a more structured and efficient workflow, enabling them to respond to threats with greater speed and accuracy. The playbooks are now published in the “SOAR essentials” solution in Content Hub and are ready for use by your SOC.
New workbook to manage tasks in the SOC
Now that tasks are integrated into the SOC’s incidents, the new tasks workbook offers a way for security teams to analyze task progress and completion, providing a comprehensive overview of all the tasks that exist in the Sentinel workspace. This is particularly important for SOC managers, as it allows them to easily monitor and manage the security workflow of their team. With a centralized view of all tasks, managers can quickly identify any bottlenecks or areas for improvement, including tasks that take the longest to complete. Additionally, a dashboard that shows tasks per incident/incidents and owner can help managers gain greater visibility into the workload of their team and allows analysts to manage their tasks in a timely and organized manner. The new Workbook allows toggling between those perspectives. The Workbook is now published in the “SOAR essentials” solution in Content hub.
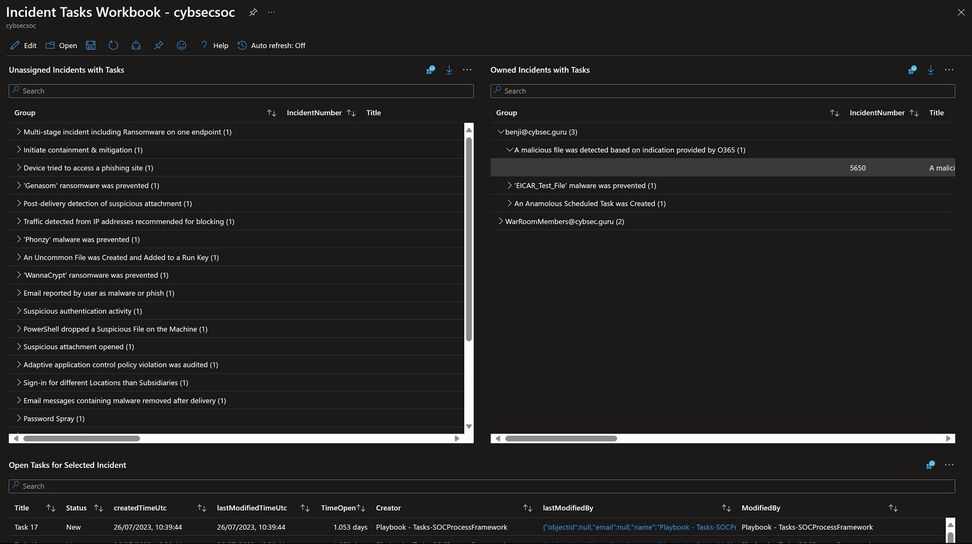
The new workbook is based on new information in Log Analytics’ SecurityIncident table. Please refer to Appendix 2 for documentation of the new tasks fields.
Tasks details in SecurityIncident table
Task details in Log Analytics can be used as dashboards to monitor task progress, investigate security incidents, and track compliance and auditing activities. The tasks details include the task name and status, task number, last completed time (in case the task was modified after it was closed), and more. If you wish to explore the new task details in the SecurityIncident table, please refer to documentation and some recommended queries provided in Appendix 2 at the end of this blog post.
Updates to the SOC Process Framework
The SOC Process Framework solution, which can be found in Content Hub, is also updated to support Tasks. With the new version, instead of writing tasks into incident comments, the SOC Process Framework will create tasks defined in the watchlist into Microsoft Sentinel Incident Tasks. As a reminder, the SOC Process Framework Solution is designed to easily integrate with Microsoft Sentinel and establish a standard SOC Process and Procedure Framework within your organization, including incident or alert tasks.
Summary
Automating task management in Microsoft Sentinel using playbooks and automation rules can help security analysts streamline their workflow and improve efficiency. Integrating Microsoft Defender workflows with Sentinel tasks provides security teams with a more structured and effective way to investigate and respond to security incidents, significantly improving an organization’s security posture. Additionally, Workbooks offer valuable insights into task progress and completion, enabling security teams to monitor their workflow and identify areas for improvement. The new SecurityIncident audits allow for full flexibility in querying tasks details and integrating them into more of the SOC’s tools.
Appendix 1: Tasks resources
Use tasks to manage incidents in Microsoft Sentinel | Microsoft Learn
What’s new: Incident tasks – Microsoft Community Hub
Appendix 2: suggested queries using the new tasks details
For documentation on managing tasks using Log Analytics: Audit and track changes to incident tasks in Microsoft Sentinel
SOC analysts open tasks per incident:
SecurityIncident
| where Owner.userPrincipalName == “<upn>”
| mv-expand Tasks
| evaluate bag_unpack(Tasks)
| summarize arg_max(lastModifiedTimeUtc, *) by taskId
| where status !in (‘Completed’, ‘Deleted’)
| order by lastModifiedTimeUtc desc
| project IncidentNumber, Title, Description, Severity, TaskTitle = [‘title’], TaskStatus = [‘status’], createdTimeUtc, lastModifiedTimeUtc, TaskCreator = [‘createdBy’].name, lastModifiedBy, ModifiedBy = [‘lastModifiedBy’].name
| order by IncidentNumber desc
Check deleted Tasks:
SecurityIncident
| mv-expand Tasks
| evaluate bag_unpack(Tasks)
| summarize arg_max(lastModifiedTimeUtc, *) by taskId
| where status == ‘Deleted’
| project TaskTitle = [‘title’], TaskStatus = [‘status’], createdTimeUtc, lastModifiedTimeUtc = column_ifexists(“lastModifiedTimeUtc”, datetime(null)), TaskCreator = [‘createdBy’].name, lastModifiedBy, TaskCloser = [‘lastModifiedBy’].name, IncidentNumber, IncidentOwner = Owner.userPrincipalName
| order by lastModifiedTimeUtc desc
To check Tasks that are re-opened:
SecurityIncident
| where IncidentNumber == 553
| mv-expand Tasks
| evaluate bag_unpack(Tasks)
| summarize arg_max(lastModifiedTimeUtc, *) by taskId
| where lastCompletedTimeUtc < lastModifiedTimeUtc
| project TaskTitle = [‘title’], TaskStatus = [‘status’], createdTimeUtc, lastModifiedTimeUtc = column_ifexists(“lastModifiedTimeUtc”, datetime(null)), TaskCreator = [‘createdBy’].name, lastModifiedBy, TaskCloser = [‘lastModifiedBy’].name, IncidentNumber, IncidentOwner = Owner.userPrincipalName
| order by lastModifiedTimeUtc desc
Check Tasks that are not completed but incident is closed:
SecurityIncident
| summarize arg_max(TimeGenerated, *) by IncidentNumber
| where Status == ‘Closed’
| mv-expand Tasks
| evaluate bag_unpack(Tasks)
| summarize arg_max(lastModifiedTimeUtc, *) by taskId
| where status !in (‘Completed’, ‘Deleted’)
| project TaskTitle = [‘title’], TaskStatus = [‘status’], createdTimeUtc, lastModifiedTimeUtc = column_ifexists(“lastModifiedTimeUtc”, datetime(null)), TaskCreator = [‘createdBy’].name, lastModifiedBy, IncidentNumber, IncidentOwner = Owner.userPrincipalName
| order by lastModifiedTimeUtc desc
Have a Windows Notebook and want Faster speeds.
Window notebook and All-in-one come with a Power setting set to balanced, but there is a Hidden way to expose to Choose the High performance mode power plan.
Go to your windows prompt and type the following.
powercfg -SETACTIVE 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c
After typing the above command, please confirm whether the High performance mode is available and selected in the power plan of Windows operating system, please refer to the following method.
Type and search [Choose a power plan] in the Windows search bar, then click [Open]. Make sure the [High performance] mode is available. Now you can configure addition setting including Process speed. If you have an Intel CPU Turbo boost will be able to reach the highest frequency.
The Aftermath of Data Breaches
| PII compromised in a data breach could be used or sold for identity theft schemes. Dark web marketplaces, forums, and websites offer a spectrum of products and services that monetize stolen personal and financial data, corporate and social media account details, as well as counterfeit documents and money. The dark web also provides an arsenal of malicious tools and malware that, combined with this personal information, can allow threat actors to create official documents or identities to commit identity theft or launch cyberattacks. Threat actors may use compromised PII to launch cyberattacks in social engineering attempts via phishing emails, vishing, SMiShing, compromised websites, and social media scams to compromise accounts, steal funds, steal additional PII or financial information, open new fraudulent accounts, access computer networks and resources, and perform additional cyberattacks. |
| For example, Charles Schwab Corp., the parent company of TD Ameritrade, Inc., recently disclosed a data breach resulting from exploited vulnerabilities discovered in the MOVEit file transfer software. The customer data stored on TD Ameritrade’s server was compromised and, therefore, impacted customers may be subjected to an increased risk of identity theft and other malicious activity. Other organizations affected by the MOVEit vulnerability to date include various financial institutions, British Airways, Shell PLC, and more. Furthermore, the Cl0p ransomware group published Shell’s data to the dark web after Shell refused to pay the ransom demand; therefore, TD Ameritrade’s data may similarly be at risk. Also, the Schwab/TD Ameritrade merger conversion is ongoing until Labor Day weekend of 2023, which may enable threat actors to target and exploit potential victims in social engineering schemes, such as fraudulent merger updates, security account alerts, and account updates. |