In collaboration with the Microsoft Threat Intelligence Center (MSTIC), we
are excited to announce Fusion
detection for ransomware is now publicly available!
These Fusion detections correlate alerts that are potentially associated
with ransomware activities that are observed at defense evasion and execution
stages during a specific timeframe. Once such ransomware activities are
detected and correlated by the Fusion machine learning model, a high
severity incident titled “Multiple alerts possibly related to Ransomware
activity detected” will be triggered in your Azure Sentinel workspace.
In order to help your analyst quickly understand the possible attack, Fusion
provides you with a complete picture for the suspicious activities happened on
the same device/host by correlating signals from Microsoft products as well as
signals in network and cloud. Supported data connectors include:
- Azure Security Center
- Microsoft Cloud App Security
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Azure Sentinel scheduled analytics rules. Fusion only
considers scheduled analytics rules with tactics information.
The screenshot below shows a Fusion incident with 22 alerts. It correlates
low severity signals that were detected around the same timeframe from the
network and the host to show a possible ransomware attack and the different
techniques used by attackers.
For more information, see Multiple alerts possibly related to Ransomware activity
detected.
Why Fusion detection for ransomware?
Ransomware attack is a type of attack that involves using
specific types of malicious software or malware to make network or system
inaccessible for the purpose of extortion – ‘ransom’. There is no doubt that
ransomware attacks have taken a massive turn in being the top priority as a
threat to many organizations. A recent report released by PurpleSec revealed that the
estimated cost of ransomware attacks was $20 billion in 2020 and with downtime
increasing by over 200% and the cost being 23x higher than 2019.
Preventing such attacks in the first place would be the ideal solution but
with the new trend of ‘ransomware as a service’ and human operated ransomware,
the scope and the sophistication of attacks are increasing – attackers are
using slow and stealth techniques to compromise network, which makes it harder
to detect them in the first place.
With Fusion detection
for ransomware that captures malicious activities at the defense evasion and
execution stages of an attack, it gives security analysts an opportunity to
quickly understand the suspicious activities happened around the same timeframe
on the common entities, connect the dots and take immediate actions to disrupt
the attack. When it comes to ransomware attacks, time more than
anything else is the most important factor in preventing more machines or the
entire network from getting compromised. The sooner such alerts are raised to
security analysts with the details on various attacker activities, the faster
the ransomware attacks can be contained and remediated. A detection like this
will help analysts by giving the compilation of attacker activity around
execution stage helping reduce MTTD (Mean Time to Detect) and MTTR (Mean Time
to Respond).
Examples of the Fusion detection for ransomware
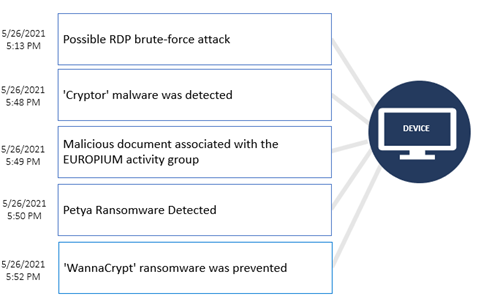
In the Incident 1
example, Fusion correlates alerts triggered within a short timeframe on the
same device, indicating a possible chain of attacks from how the attackers got
in through possible RDP brute-force attack, followed by the use of a ‘Cryptor’
malware and potential phishing activities using malicious document associated
with the EUROPIUM activity group, to the detection of Petya and WannaCrypt
ransomware in the network.
Incident 1
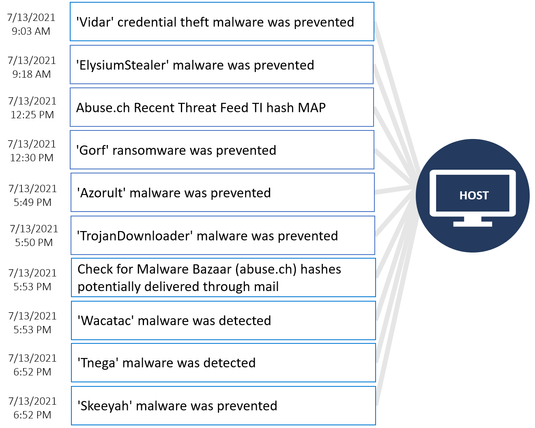
Incident 2
below is another example of the Fusion ransomware detection that was confirmed
as true positive. This incident correlates alerts showing ransomware activities
at defense evasion and execution stages on the same host, along with additional
suspicious activities detected during the same timeframe to show you possible
techniques used by attackers to compromise the host.
Incident 2
In these Fusion incidents, the alerts related to ransomware/malware
detection might indicate that the ransomware/malware was stopped from
delivering its payload but it is prudent to check the machine for signs of
infection. Attackers may continue malicious activities after ransomware was
prevented – it is also important that you investigate the entire network to
understand the intrusion and identify other machines that might be impacted by
this attack.
What’s next after receiving the Fusion detection?
After receiving Fusion detentions for possible ransomware activities, we
recommend you to check with the machine owner if this is intended behavior. If
the activity is unexpected, treat the machine as potentially compromised and
take immediate actions to analyze different techniques used by attackers to
compromise the host and to evade detection in this potential ransomware attack.
Here are the recommended steps:
- Isolate the machine from the network to prevent
potential lateral movement. - Run a full antimalware scan on the machine, following
any resulting remediation advice. - Review installed / running software on the machine,
removing any unknown or unwanted packages. - Revert the machine to a known good state, reinstalling
operating system only if required and restoring software from a verified
malware-free source. - Resolve to recommendations from alert providers (e.g. Azure Security Center and Microsoft Defender) to prevent future breaches.
- Investigate the entire network to understand the
intrusion and identify other machines that might be impacted by this
attack.
As you investigate and close the Fusion incidents, we encourage you to provide feedback
on whether this incident was a True Positive, Benign Positive, or a False
Positive, along with details in the comments. Your feedback is
critical to help Microsoft deliver the highest quality detections!