Here some new Technology that i have come across
PuriFile
PuriFile’s software suite provides market-leading inspection
and sanitization of digital files, preventing the loss of critical data and
ensuring business continuity for government and commercial customers. Built to
protect your inbox and halt release of sensitive information, PuriFile
inherently understands your email, Microsoft Word, PowerPoint, Excel, PDF, and
image files, so it can provide thorough email and file inspection and
sanitization while maintaining the integrity of your network and information.
Microsoft Exchange Server (MXS) is a collaborative
enterprise server application designed by Microsoft to run on Windows Servers.
MXS supports organizational email, contacts and tasks, calendar, data storage
and web based and mobile information access. By residing on an organizational
endpoint – the Exchange Server, PuriFile can provide email security through identification
and remediation of content entering and exiting through your organizations
communication lifeline, provide Data Loss Prevention and mitigate Zero-Day
attacks.
How it Works
Exchange Server Plugins – Microsoft provides an Application
Programming Interface (API), as well as information and resources to extend
Microsoft Exchange Server allowing for the customization of a unique customer
focused email environment.
PuriFile Exchange Plugin – Using the Exchange Server API, the
PuriFile plugin provides Data Loss Prevention, limits Zero-Day attacks and
controls content leaving an organization.
Highly configurable, PuriFile is capable of identifying content within
email and attachments based on well-defined policies and takes corrective
action to alert the recipient and sender to remediate violations.
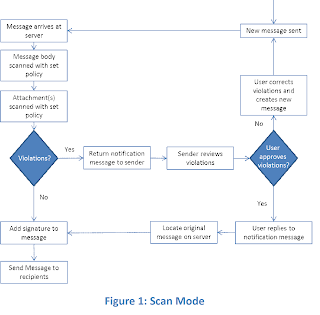
Message Scanning – Residing on a corporate exchange server,
PuriFile is capable of scanning incoming and outgoing email to identify suspect
content based on an organizational policy. When an individual receives an email
or attempts to send email to a recipient, the PuriFile engine scans the content
and attachments checking for violations. In the event a violation is detected,
the recipient/sender is alerted and is able to take corrective action to accept
or modify the content prior to it being received or sent to the recipient:
Figure 1: Scan Mode
Removing Attachments – In addition to the normal email
message scanning, PuriFile is able to provide scanning and insight into content
residing in email attachments. When an individual receives or completes an
email and attempts to send it to the recipient, PuriFile scans the message
along with any attachments and checks for violations. In the event of a
violation in the attachment, the PuriFile engine replaces the content with a
text file identifying the violations. A return notification is sent back to the
sender along with the text file of violations.
The user will then be given an opportunity to review the violations and
address as appropriate. Once all violations are addressed, the email is
reprocessed for reading or sent on to the recipient:
Figure 2: Attachment Mode
Message Cleansing – The Message Cleansing mode is similar to
Replacing Attachments mode. Rather than alerting the recipient/sender of
content in violation, the Message Cleansing capability cleanses the offending
content from the document. When an individual receives or completes an email
and attempts to send it to the recipient, PuriFile scans the message along with
any attachments and checks for violations. In the event of a violation in the
attachment, the PuriFile engine removes the content from the file prior to
reading or sending the offending file.
Figure 3 – Cleanse Mode
The added effect of the cleansing operation removes any
malicious content, effectively halting in excess of 90% of zero-day attacks.
Combined with an effective Anti-Virus/Anti-Malware solution organizations will
have gained the upper hand on virulent viruses and malware.
Here is a cool offer if you interested in testing this let me know i will forward you info to the Beta test team. They are offering to get the software for 12 months (plus
support) for doing the beta test for us.
Send email to Jferron @ Interactive Security Training.com (NO spaces)